Tag: Linux Server
-
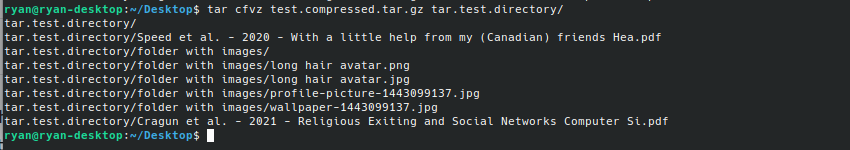
Linux Server – tar files and directories
I recently had to move all my websites from one virtual private server (VPS) to another. When I only had a few such websites, I was okay with using SFTP (via Filezilla) to download all of the files and then upload them to the VPS. It took a while but I was okay with that.…
-
Linux – Setting Up FTP/SFTP Restricted Access for User
I run a server (Ubuntu 18.04) that hosts about a dozen websites using Linode. Most of the sites are run using WordPress and are my own or sites I manage for friends or family. I do, however, host one for a colleague who actively develops online content for that site. As WordPress has developed, the…
-
Virtual Private Hosting – How to Remove a Domain with Certbot SSL Certificate (on Ubuntu 16.04 with apache)
It used to be pretty easy to remove a domain from my Virtual Private Server – dissable the site in apache, delete the files, delete the underlying database, and remove the domain from my DNS manager. Done. With SSL certificates now a standard part of hosting websites (see here), this is complicated by the removal…