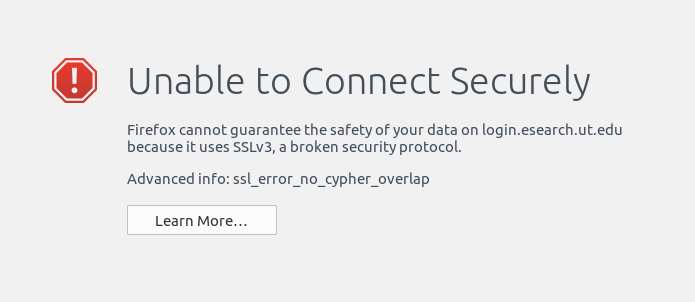
Generally speaking, it’s a bad idea to override security protocols browsers have instituted as they are designed to keep you safe on the internet (in the “less likely to be hacked” sense). However, with a recent update to Firefox 34, a website I use all the time for my research that is run by my university was no longer allowing me to login. Instead, I was receiving this message:
Since I know the website is safe (I’ve used it thousands of times over the last seven years), I needed to bypass this security protocol in Firefox. After some googling for solutions, I found one, but it wasn’t very clear. So, here’s what I did with screen captures for assistance…
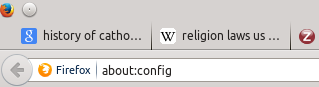
1) Open a new tab in Firefox and type “about:config” in the URL bar (without the quotes, of course):
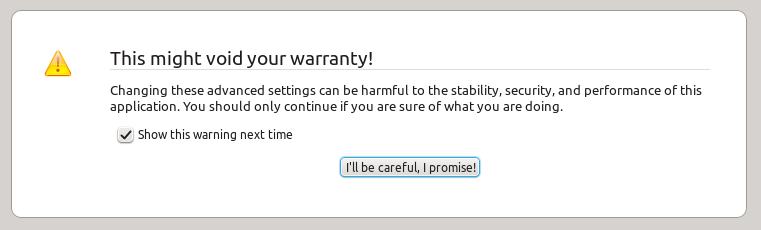
2) You’re likely to get another warning message saying “This might void your warranty!” (see screen capture below) Firefox is trying to keep you from making changes to the underlying settings of the browser. Promise to be careful and move on:
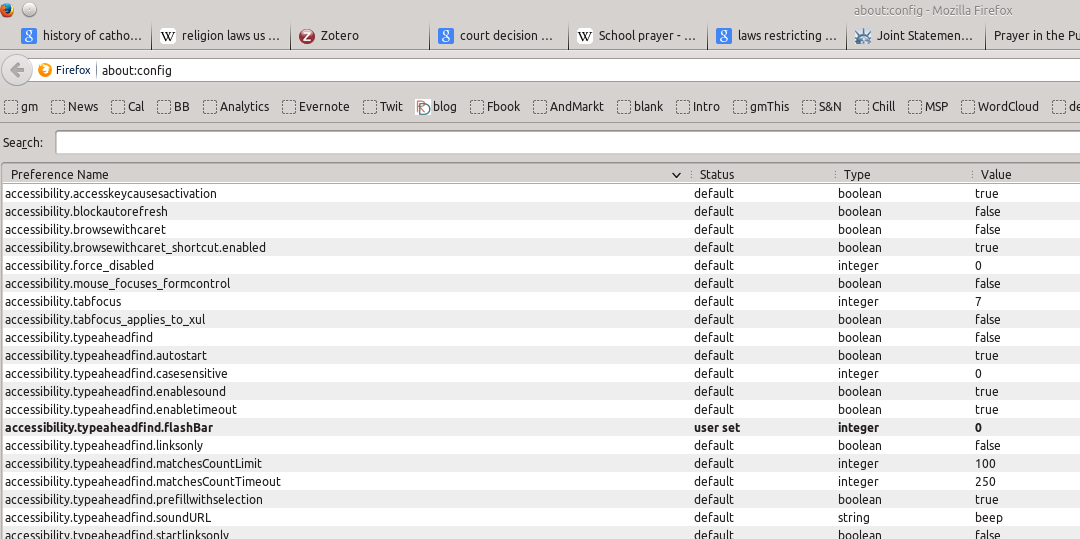
3) Once you click on the “I promise to be careful” button, you’ll see a search box and a huge list of settings:
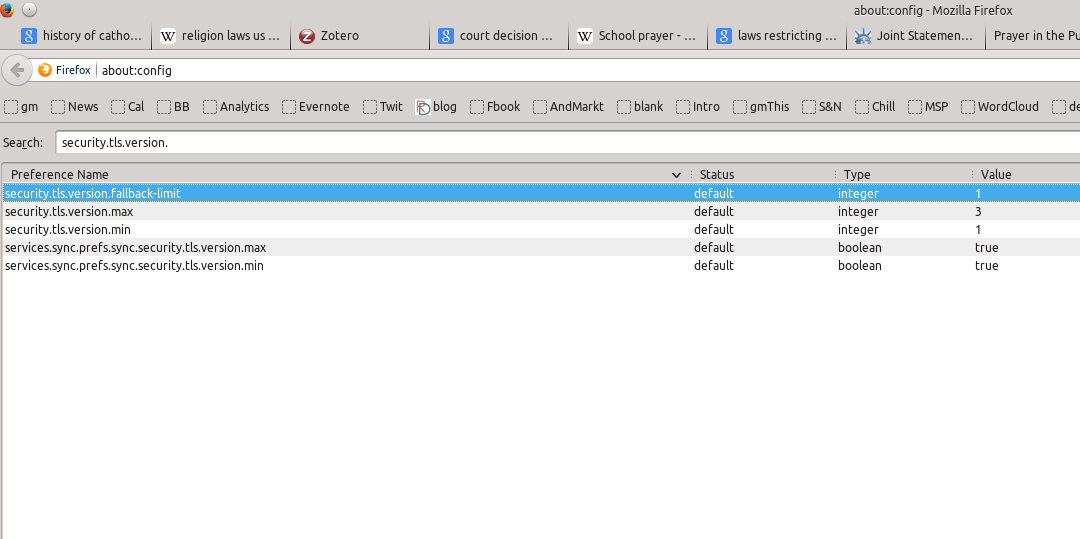
4) In the search bar, enter the following (without the quotes): “security.tls.version.”:
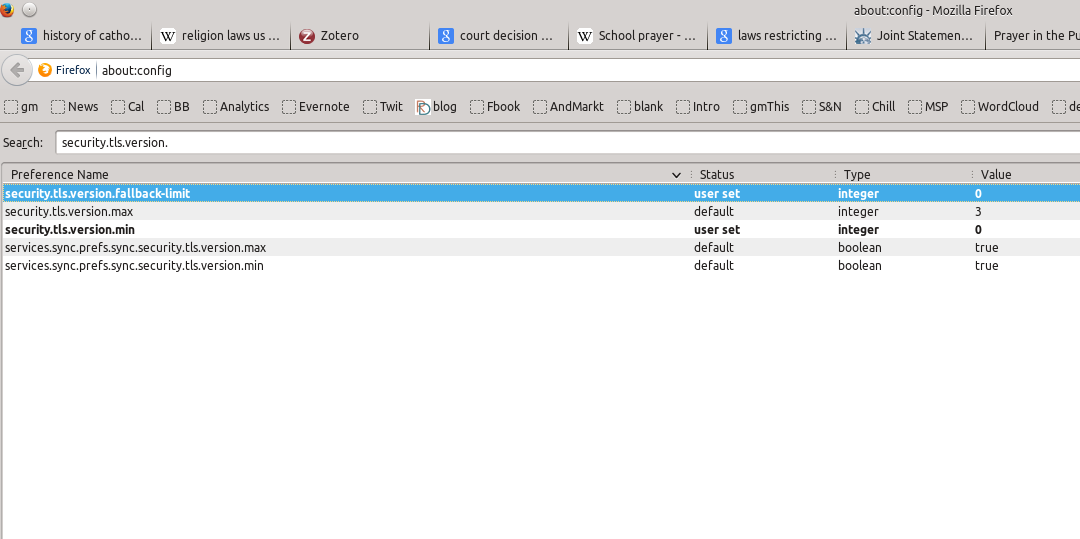
5) You’re going to change two of those settings. First, right-click on the setting “security.tls.version.fallback-limit” and select modify. You’re going to change the “1” to “0”. Then do the same thing with “security.tls.version.min”, changing the “1” to “0”. You should now see the following:
6) Now trying loading the page that was giving you the security warning. It should load.
NOTE: Keep in mind, you have now made your browser less secure. Really what you should do is contact the administrator of the website that isn’t loading and tell them that they need to update their security on the website so you don’t have to expose yourself to greater security risks. But, if this is an essential website for you to use in the meantime, this should get you around the issue.
![]()
Leave a Reply