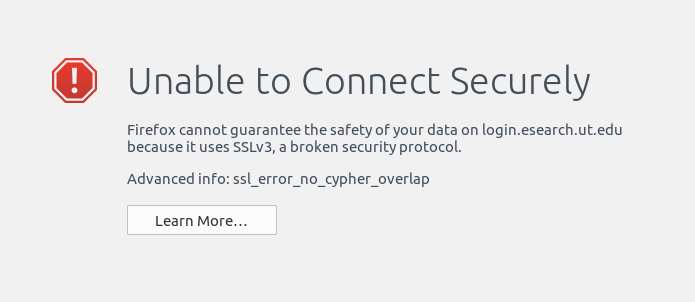
Generally speaking, it’s a bad idea to override security protocols browsers have instituted as they are designed to keep you safe on the internet (in the “less likely to be hacked” sense). However, with a recent update to Firefox 34, a website I use all the time for my research that is run by my university was no longer allowing me to login. Instead, I was receiving this message:
Since I know the website is safe (I’ve used it thousands of times over the last seven years), I needed to bypass this security protocol in Firefox. After some googling for solutions, I found one, but it wasn’t very clear. So, here’s what I did with screen captures for assistance…
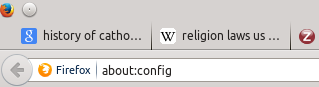
1) Open a new tab in Firefox and type “about:config” in the URL bar (without the quotes, of course):
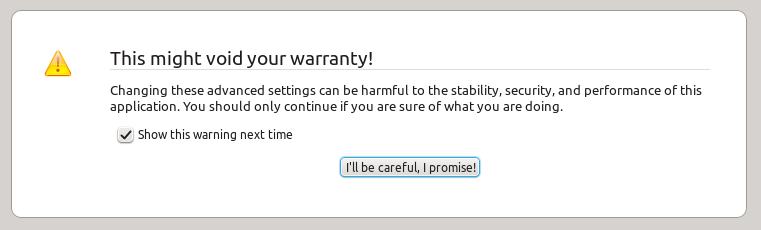
2) You’re likely to get another warning message saying “This might void your warranty!” (see screen capture below) Firefox is trying to keep you from making changes to the underlying settings of the browser. Promise to be careful and move on:
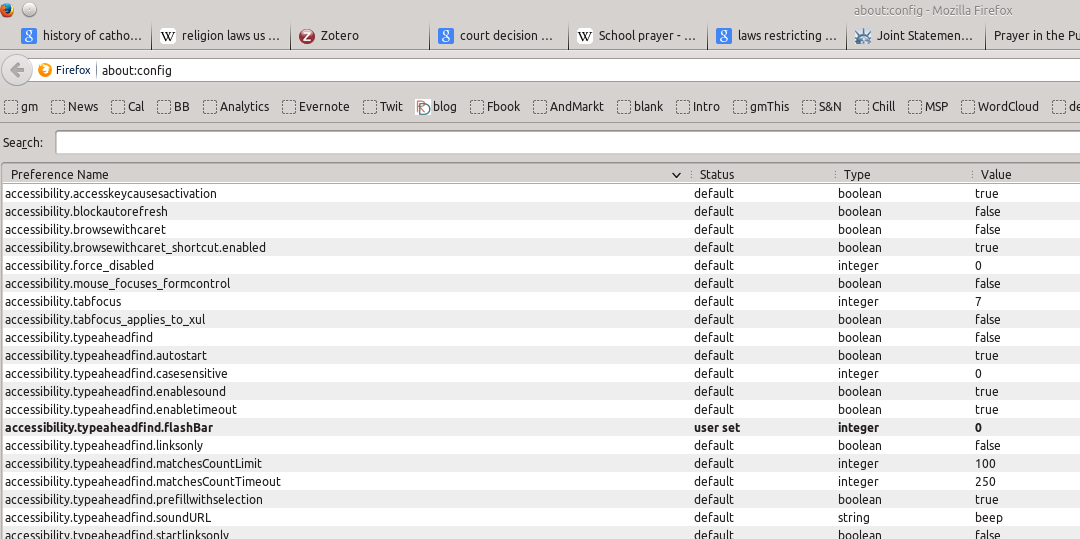
3) Once you click on the “I promise to be careful” button, you’ll see a search box and a huge list of settings:
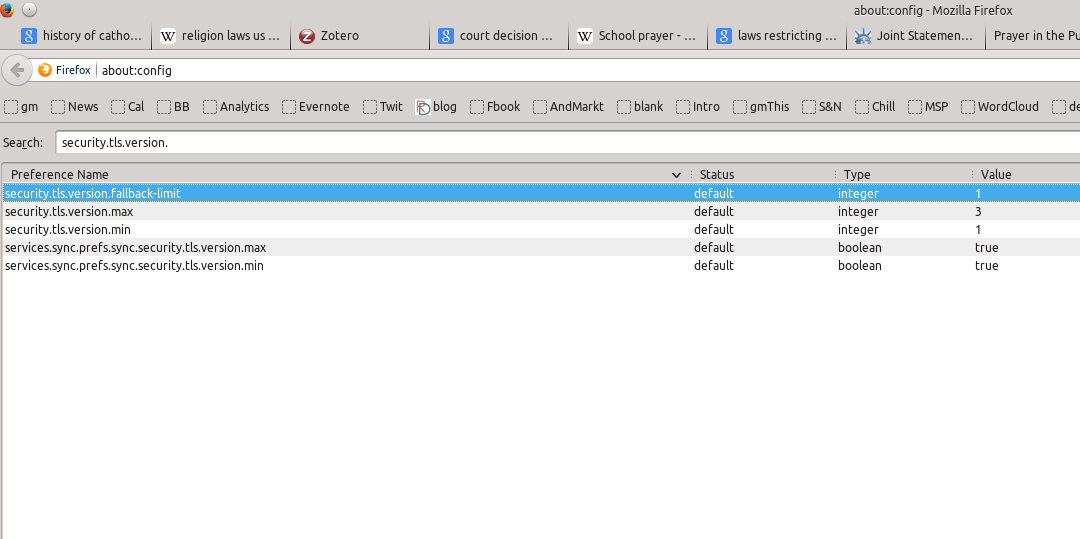
4) In the search bar, enter the following (without the quotes): “security.tls.version.”:
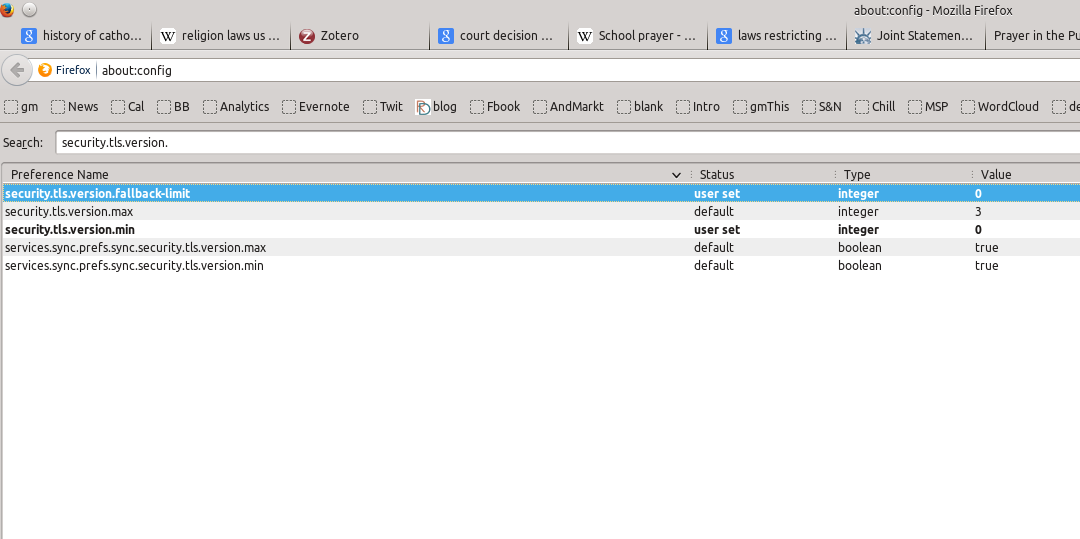
5) You’re going to change two of those settings. First, right-click on the setting “security.tls.version.fallback-limit” and select modify. You’re going to change the “1” to “0”. Then do the same thing with “security.tls.version.min”, changing the “1” to “0”. You should now see the following:
6) Now trying loading the page that was giving you the security warning. It should load.
NOTE: Keep in mind, you have now made your browser less secure. Really what you should do is contact the administrator of the website that isn’t loading and tell them that they need to update their security on the website so you don’t have to expose yourself to greater security risks. But, if this is an essential website for you to use in the meantime, this should get you around the issue.
![]()
Sadly, even this didn’t help – could you please check whether *your* Firefox can access after the fix you describe? (An older Opera version has no problems with that site.)
Thanks!
Hi Daniel,
You’re correct. That site is still not loading even with the changes in place. Not sure why it isn’t working. My only suggestion would be to try adjusting some of the other SSL settings (in the about:config window of Firefox, type “security.ssl” and you’ll be able to see about 20 different options that you could modify to see if they allow you to access that site). If you figure it out, please come back and post here to let us know what worked.
the first setting that was said to change from 1 to 0 on my pc was at 3 changing to 0 did not work but changing it to 1 {from 3} worked.
Thank you that worked for me.
This worked for me too. Thank you very much!
In windows10 it was not possible logging in in https://“remote draytek router”:443.
This solution fixed the job.
Had the same issue accessing our Draytek on 8.1. Once again, this solution fixed the problem on Firefox. Very many thanks!
thnx man!
Problem is that – after a look at the traffic via Wireshark – FF34 still sends “SSL 3.0 Client Hello” (Version: SSL 3.0 (0x0300)) while the server then responds with a “Level: Fatal – Handshake Failure”, and FF just displays the erroneous message about “Firefox cannot guarantee the safety of your data on localhost because it uses SSLv3, a broken security protocol.”, which is completely rubbish. This is clearly a bug in FF.
Thanks Man!
Thanks you for diagnosing this problem and having the patience and kindness to publish it.
Thank you for the instructions, this worked.
The procedure described here works perfectly for my case: I had a configuration page for a server with limited possibilities to manage certificates (only a self-signed certificate was available) that was no longer working after latest updates of firefox and chrome. Now it works again.
Thanks a lot!
Aldo
You can globally re-enable connecting to ssl by going into about:config
search for the preference named security.tls.version.min. double-click it, change its value to 0 and restart the browser.
(Error code: ssl_error_no_cypher_overlap) how to overcome?
Thanks a lot, this helped me log in to our old unsecure UPS adminpage 🙂
Thanks a lot
Worked Thank u
Thank you, perfect. It worked
i used internet explorer to access the site that fire fox would not let me access due to the error code and had no problem
Thanks — I just ran into this problem and your fix worked.
thanks bro
Thanks a million for the solution. I had been trying all day to enter a page of the Tax Dept and kept getting the error message. I tried your solution and it worked first time. I also reset the changes back to normal afterwards. Thanks again, this was very important for me.
Great! I have tried several fixes with no luck. This one worked. Thank you!
Thanks, this worked, but:
” Really what you should do is contact the administrator of the website that isn’t loading and tell them that they need to update their security on the website so you don’t have to expose yourself to greater security risks.”
Can someone tell American Airlines that?
Ryan, you say you know the website is safe, but in fact it is not. It is still using SSL v3.0 which is vulnerability not just for you but for the website as well. The only way to make it safe is to convince the administrators to stop allowing SSL v3.0, not to bypass the browsers protections. The fact that you know the website operators have no bad intentions is not relevant, as this vulnerability can be exploited without the cooperation of the website administrators, or even of anyone connect with the website. If you do have to access the website, please turn the protections back on when you are finished.
Alas, I don’t. The reason why I was figured it out on Firefox was because I couldn’t figure it out on Chrome. Do you really need to use Chrome on that website? If so, another option would be to use an older version of Chrome. You could set up a virtual machine using something like Virtual Box and install an older version of Chrome on that. That would get around it if you really need to. Not sure what to tell you with the latest versions other than to tell the website host to update their site.
This worked perfectly on firefox.
However, I’m having the exact same problem in Google Chrome but it presents itself as a timeout limit error. I have uninstalled/reinstalled, restarted, and even performed a system restore and the problem persists on Chrome for the same website with https which now works on Firefox due to your fix.
Do you have any suggestions to make this fix on Chrome? I would appreciate it.
Thank you for publishing this. It fixed my problem accessing a local utility site.
Excelente, me funciono para la siguiente url “
This is bad advice. You should add the domains you want to bypass to this about:config entry: security.tls.insecure_fallback_hosts
Separate them by commas. See the solution here – https://support.mozilla.org/en-US/questions/1058193#answer-719770
This allows you to *only* bypass the security for sites you trust/must access. Not for everything.
this is working fine for me
THANK YOU! THANK YOU! THANK YOU! This did the trick to reach my Juniper SSGs.
Thanks very much Lucy! 🙂 This worked perfectly for me (I’m using a firefox portable)
Many thanks Lucy, your post did help me a lot…
Thanks Lucy. Adding hosts (I added IPs in my case) in security.tls.insecure_fallback_hosts finally allowed me to bypass this error. All other suggested fixes did not work.
Good Answer!
Used it myself.
the combination of you and lucy solved my problem. many and much thanks to you both. well, lucy, that’s better advice. (p.s. after my successful login, i removed the domain from security.tls.insecure_fallback_hosts and it still worked – i think i have had a ‘bad’ certificate)
anx
Thank you for the steps.
thank you
No with Firefox version 39 they have “fixed” this solution. Still not working 🙁
Thanks!!! It works!!!
Explanation and advice by Lucy (above comment) seems wise. However it needs to be tested!!! The hack mentioned in the post is perfect :)!!!
you’re fantastic!
Thanks a lot!
The solution posted in this article previously worked for me, but no longer works in version 39.0. I gave up looking for a fix and went with a different browser.
I was unable to open most of the https sites on my computer at college lab. The computer runs Firefox 12.0. This version of Firefox does not have the options “security.tls.version.” and “security.tls.version.min”. Instead it had the option “security.enable_tls”. It was set to ‘false’ by someone. Toggling it to ‘true’ made the https sites load.
This worked for me .Thanks a lot.
please add -keyalg RSA while generating key . this will solve the problem
You sir are the greatest person to have ever lived! worked like a charm. 😀
Only security.tls.insecure_fallback_hosts worked for me – thanks Lucy!
If it doesn’t work just set this option security.tls.unrestricted_rc4_fallback;true
and that’s it!
🙂
You sir are a genius!!! NOTHING worked on here but your suggestion/solution worked!!!
For me works following:
security.tls.version.fallback-limit;1
security.tls.version.max;3
security.tls.version.min;1
services.sync.prefs.sync.security.tls.version.max;false
services.sync.prefs.sync.security.tls.version.min;false
I completed the following and it worked for me:
1. security.tls.unrestricted_rc4_fallback – toggled to true
2. security.tls.version.fallback-limit – set to “0”
3. security.tls.version.min – set to “0”
Ryan, thanks for the nudge in the right direction!
This exact setup worked for me as well.
With Firefox 50.0 none of the above mentioned advices worked for me. I’m still staying unable to log into my local area network connected SNOM370 IP phone.
Update — the RC4 support has been completely removed in FF50 as stated in https://www.fxsitecompat.dev/en-CA/docs/2016/rc4-support-has-been-completely-removed/. Yep, owing to this paternalism by Mozilla, I cannot HTTPs my phone next to me.
Yes, it appears that you really need to keep the Firefox 49.0.2 installer on hand now. Turn off all updating, install 49.0.2 and add the domains you want to bypass to about:config entry: security.tls.insecure_fallback_hosts (Thanks, Lucy!)
The solution from Bryan (10/13/2016) did work for me too. I had firefox 51, downgraded to firefox 49 and implemented solution.
Thx for clearification about dropped RC4 support in version 50. I was struggling with problems for weeks.
I solved it temporarily be using an old IE to access the two sites causing me problems.
Hiya! Sadly when I typed in “security.tls.version.” It did not work 🙁 and I have a report due soon! Any suggestions?
(and yes I typed it without the quotations)
I just checked in the latest version of Firefox and it still pulls up. Did you type “about:config” in the browser URL bar first? Then, in the Search box below that, search for security.tls.version? If so, you should find it.
I used a old copy of Firefox-Portable I still had from 2013. It is version 21, so it connected with no changes needed.
None of these workarounds — absolutely *NONE* of them — works with FF 56. Looks like I’m stuck forever with “ssl_error_no_cypher_overlap” if I want to keep using FF, particularly whenever I try to log into Amazon.com
Utterly absurd.
worked…thanks
Amazing! A straight forward, easy to follow solution that actually works. I just updated to Firefox 62.?, the UN was diddling with the Internet over the weekend, and the Sunnyvale crud were pre-election deleting conservative sites . I still don’t know what caused the problem, but it is now avoided. I’m using Kaspersky so hope it helps with security.
?
This error can also be caused by BT Webprotect blocking a site by mistake, so if you are with BT this is worth checking too.
Hello am using firefox3.6.28 the error still persists despite am using windows cp so i cant update to the latestet version any assistance